NIST and Quantum Computers posted February 2016
A few weeks ago, NIST released a draft on their report on Post-Quantum Cryptography.
As we all know, some things are happening in the quantum computing world. Some are saying it will never work, some are saying it will but that it will take time until large enough quantum computers could break today's crypto.
So reading this paragraph taken from the NIST document, it can make sense on why we would want to move today to post-quantum crypto:
Historically, it has taken almost 20 years to deploy our modern public key cryptography infrastructure. It will take significant effort to ensure a smooth and secure migration from the current widely used cryptosystems to their quantum computing resistant counterparts. Therefore, regardless of whether we can estimate the exact time of the arrival of the quantum computing era, we must begin now to prepare our information security systems to be able to resist quantum computing.
Let's see where is this number coming from. SSL/TLS, its protocol or its implementation, its coverage or its efficiency, has been a huge mess so far:
-
In 2009, 7 years ago, moxie introduced SSLStrip at Blackhat, a technique to render https completely useless without preloaded HSTS.
-
It's only in 2013, 3 years ago, that facebook finally made the whole app https-only just blows my mind. And that's not thinking of the myriad of companies, commerce, banks and other websites that were all accessible through http back then.
-
Nowdays most websites are still vulnerable to moxie's 2009 attack. Think about it, TLS is supposed to protect the communications against a passive and an active attacker on the network. In the passive case, I think it succeeded (in most cases). In the active case? Even HSTS or HPKP can still be somehow circumvented. Only browsers are fully capable of protecting us nowadays.
- And this is ignoring all the horrible implementations flaws like heartbleed, the broken cert validations of browsers, the broken basicConstraints of most CAs...
We could also talk about the deprecation of md5 and sha1, but sleevi does that better than me:
-
1996, 20 years ago, researches recommend to switch from md5 to sha1 because of recent advances.
-
2013, 17 years after the recommendation, Apple finally removes its support for MD5 in certificates.
- We're still in the middle of deprecating sha1, and it's a mess.
(there's also a graphical timeline made by ange: here)
Or what about the deprecation of DES? Or RC4? Or 1024 bit DH? ..
To come back to the NIST's report, here's a nice table of the impact of quantum computing on today's algorithms:
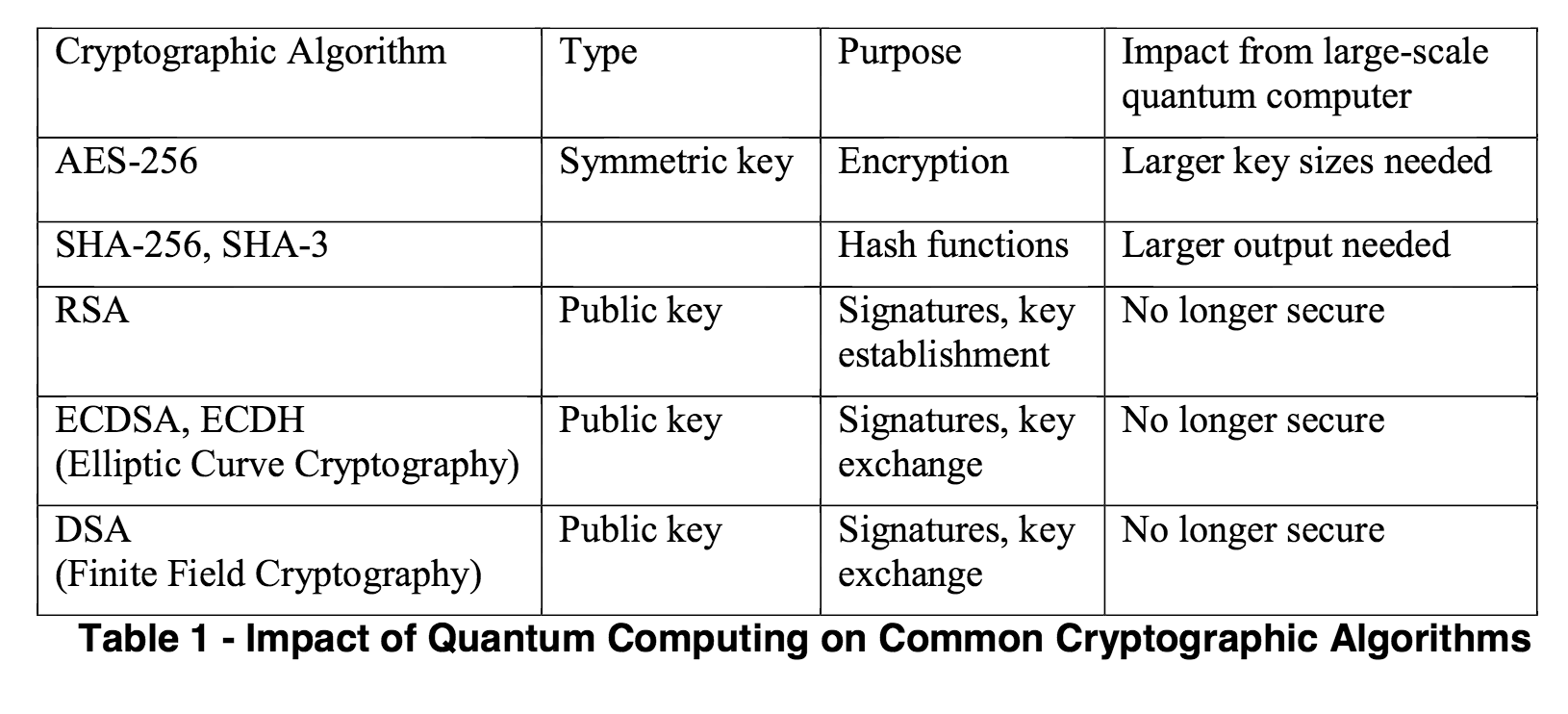
sums up pretty well what djb wrote:
Imagine that it's fifteen years from now. Somebody announces that he's built a large quantum computer. RSA is dead. DSA is dead. Elliptic curves, hyperelliptic curves, class groups, whatever, dead, dead, dead.
Contrarily to the european initiative PQCrypto, they seem to imply that they will recommend lattice-based crypto whenever their new suite B will be done. I find hard to trust any system's security proof that rely on lattice's theorical bounds because as it is known with LLL, BKZ and others: practical results are way better than these theorical limits. I don't know much about lattice crypto though, and I would you out to this paper in my to read list: Lattice-based crypto for beginners.
They agree on Hash-based signatures (which are explained in a 4 posts series on my blog), which is timy because a new version of the RFC draft for XMSS has came out, which might be the most polished hash-based signature system out there (although it is stateful unlike SPHINCS).
The paper ends on these wise words that explains how security estimation works (and has always worked):
We note that none of the above proposals have been shown to guarantee security against all quantum attacks. A new quantum algorithm may be discovered which breaks some of these schemes. However, this is similar to the state today. Although most public-key cryptosystems come with a security proof, these proofs are based on unproven assumptions. Thus the lack of known attacks is used to justify the security of public-key cryptography currently in use.
To talk about quantum computing advances, I don't know much about it but here are some notes:
-
Shor’s algorithm (the one that breaks everything) was born on 1994.
-
Late 1990s, error correcting codes and threshold theorems for quantum computing. Quantum computing might be possible?
-
2011, "the world's first commercially available quantum computer" is released by D-Wave. I believe this angered many people because this wasn't really quantum computing.
- 2015, Google and NASA have D-wave computers.
To finish this blogpost, a few things I remember from last month Real World Crypto conference:
-
Tanja asked the first speaker presenting the blackphone about quantum crypto. His response: "post-quantum right now is marketing". People laughed.
- On day 3, str4d announced that they wanted to move to post-quantum algorithms for i2p (a thing like Tor). People did not receive that as a good news. I heard people quoting djb's "crypto should be boring" line.
There is definitely a skepticism in the crypto world about quantum computing, as there is a gold rush into designing new post-quantum crypto.


Comments
Mok-Kong Shen
I have recently collected some quotes from literatures largely in question of the feasibility of sizable quantum computers (together with a few humble opinions of mine) in http://s13.zetaboards.com/Crypto/topic/7457176/1/
David
Also PQCrypto is happening now in Fukuoka https://pqcrypto2016.jp/
leave a comment...