WhibOx part 4: Whitebox crypto, vendors' perspective posted August 2016
Mike Wiener, an employee at Irdeto, the company who acquired Cloakware (the pioneering company of whitebox crypto), started this part.
The security of Whitebox comes from the fact that details are kept secret. Most implementations of working whiteboxes are proprietary.
Imagine that you want to obfuscate AES. The idea is that AES is essentialy a huge permutation. You could replace all the code with a huge look up table that would give you an output for some particular input. You could give that to someone and he would not be able to recover the key... BUT it's completely impractical.
Wiener sees whitebox crypto as not totally "crypto". More at the intersection of software security and cryptography.
Wiener said that Chow et al. brought us the 1st generation of WBC. Then Billet et al. found the first attack.
They then made a 2nd generation of whitebox crypto, but they can't talk about it.
Barak et al. proved that there exist programs that cannot be protected. Some people concluded that WBC can't work, which is not true: we don't need to protect ALL programs!
Their 2nd generation of WBC resisted to attacks from Billet et al. but were still vulnerable to DFA and DCA (Differential Computation Analysis). So they made a 3rd generation of WBC! Resistant to DFA and DCA.
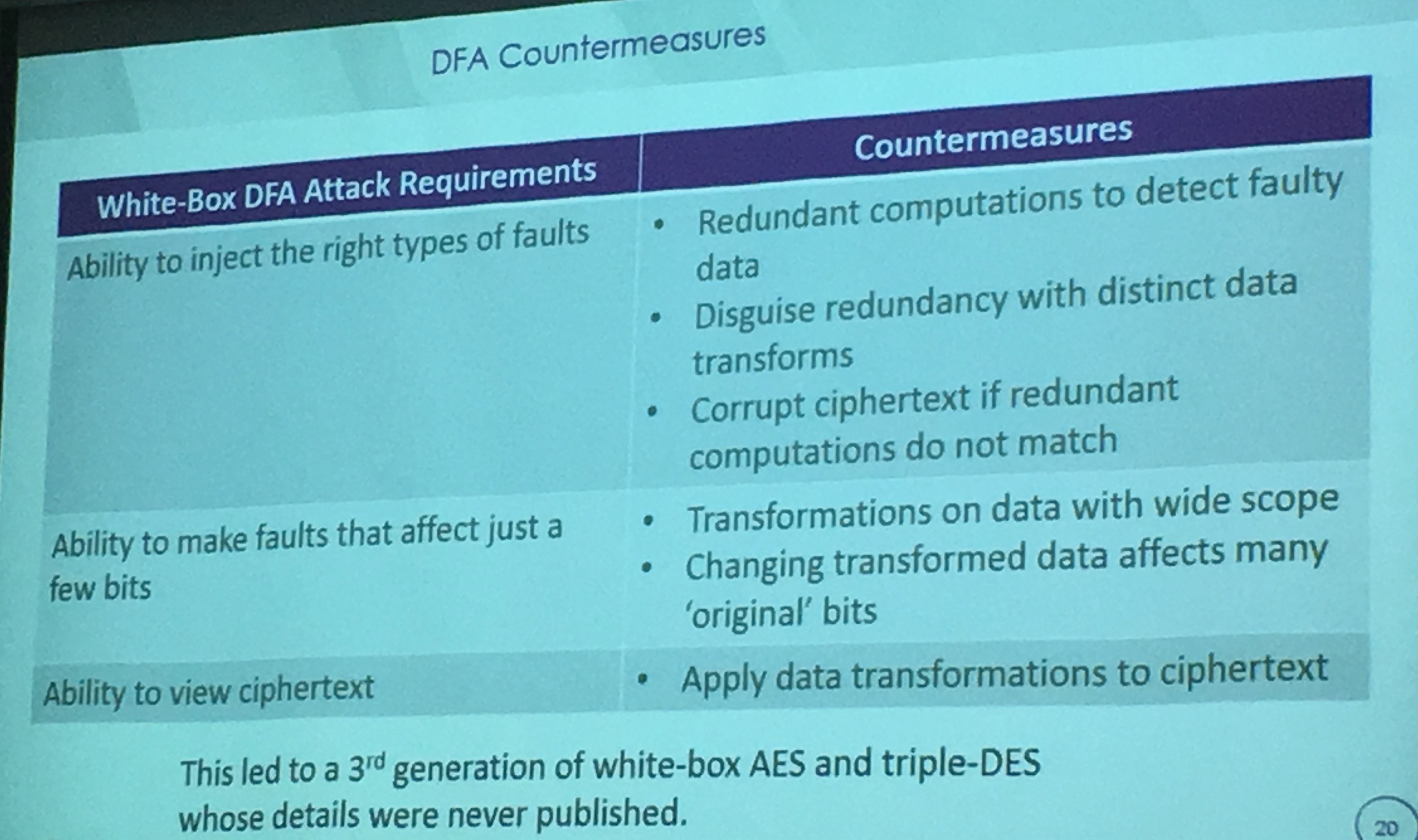
Details of this 3rd generation were never published (proprietary), they even debated about showing this slide. I won't comment on this, I'm just glad that someone from the industry came and tried to share a bit about what they did.

Wiener said hey had some success countering DCA. "SOME SUCCESS"
And NOW THEY HAVE A 4TH GENERATION!!! with improved resistance. They have new attacks (that they don't want to talk about) and so they're looking for ways to protect against these.
They think iO might be an answer in the future. They need to implement these whitebox solutions RIGHT AWAY for their clients. They don't have the luxury of waiting for better solutions.

they have designs for each of the public-key crypto algorithm! But they don't want to talk about it either. Remember, no asymmetric whitebox design is publicly known.
Also: not a lot of people talk about variable key designs, we always talk about whitebox in the context of "fixed-key". They have variant-key designs. oh oh oh!

They're now trying to get rid of tables. See picture above. They also think secure elements in hardware are not the full answer. In a software-dominated world, the need for softaware protection is unavoidable
Brecht Wyseur - Let's get real! We need WBC and Io
DRM vs CAS:
- DRM: restricting access
-
CAS: granting access
- DRM: microsoft playready, apple fairplay, marlin intertrust
- CAS: nagra (kudelski), cisco, irdeto, verimatrix, china digital tv, widevine (A google company)
How to do fast WBC? Why not ditching AES and standardized algorithms and use new algorithms that also takes advantage of the platform (SIMD, CPU, ...). But often, you need to comply to the standards.
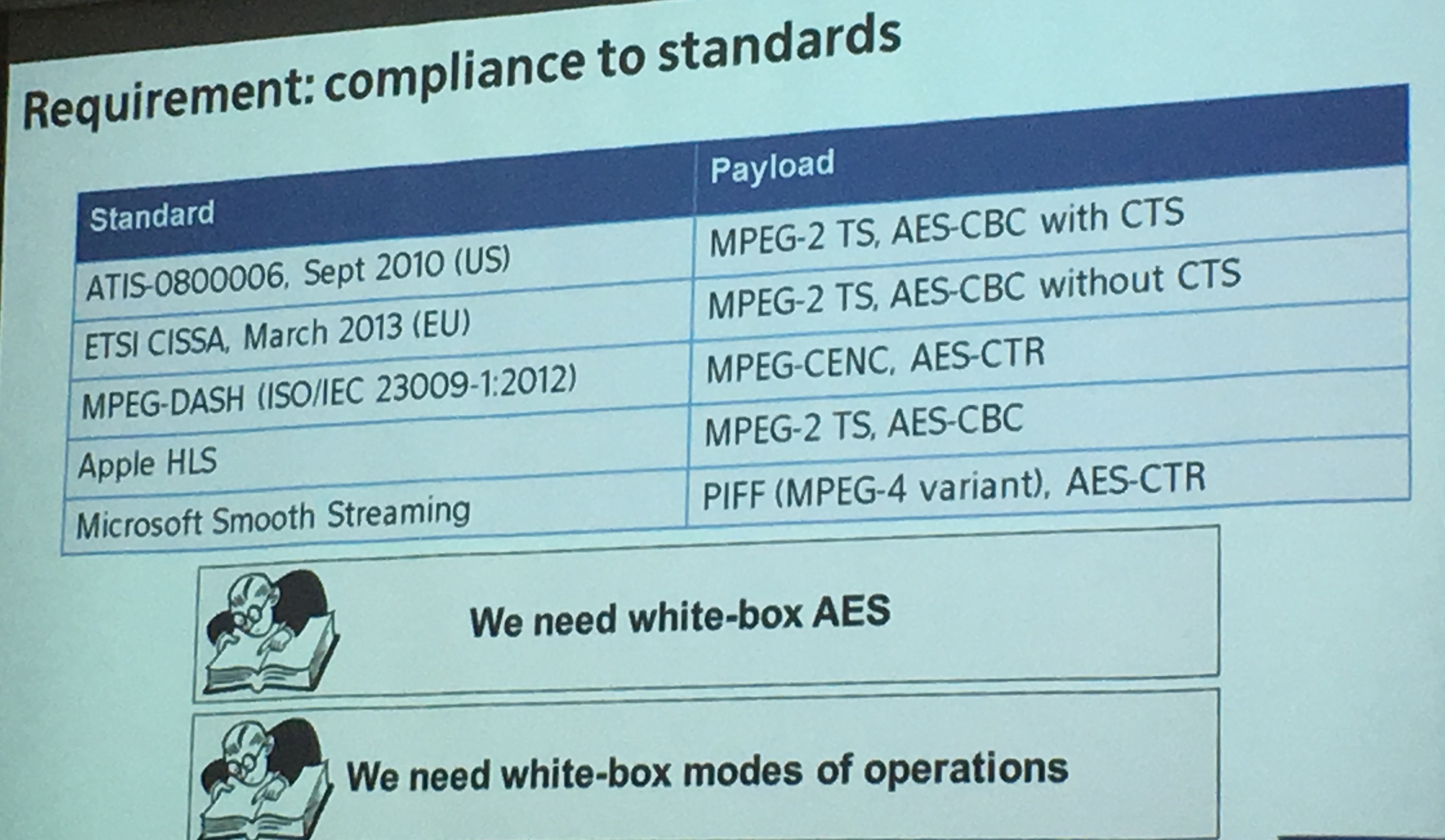
People also tend to forget modes of operation, we need to whitebox them as well.

A lot of companies are using whitebox crypto! They want evaluations or certifications. That might be a reason why we have a whitebox workshop :)
There are many other vendors in the area (arxan, whitecryption, metaforic (inside secure), irdeto, ...). But we don't really know how secure they are. It's mostly security through obscurity.
10% of banks do that in-house, 90$ use third-party tools
No certifications exist, no certifications exist, no certifications exist
Panel
- Mike Wiener: the doors of our homes are unsecure and yet the world works. I think this where we are with whitebox crypto
- someone else: you need to look at the amount of money bad guys can put into this to know how secure your whitebox crypto should be
- Marc Witteman: when the hardware security in mobile phones will be more common, WBC will become less relevant
- Pascal Paillier: outside of hardware, there is no pure software solution
- someone is saying: we had the same problems years ago with side-channel attacks on hardware, and we ended up implementing standards algorithms like AES with side-channel countermeasures (that work more or less). non-standard algorithms is a bad idea


Comments
leave a comment...