A New Public-Key Cryptosystem via Mersenne Numbers posted June 2017
A new paper made its way to eprint the other day.

a lot of keywords here are really interesting. But first, what is a Mersenne prime?
A mersenne prime is simply a prime \(p\) such that \(p=2^n - 1\). The nice thing about that, is that the programming way of writing such a number is
(1 << n) - 1which is a long series of 1s.
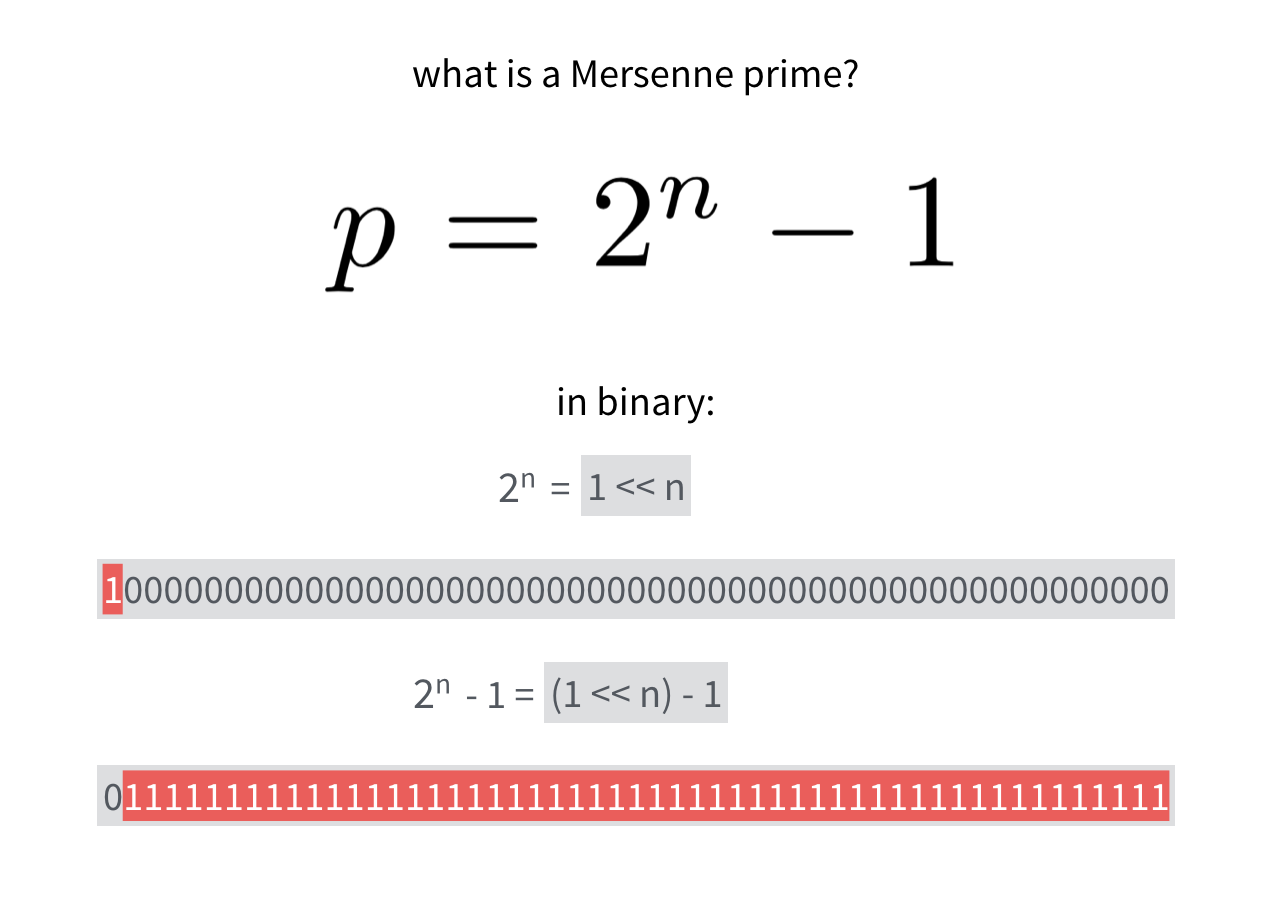
A number modulo this prime can be any bitstring of the mersenne prime's length.
OK we know what's a Mersenne prime. How do we build our new public key cryptosystem now?
Let's start with a private key: (secret, privkey), two bitstrings of low hamming weight. Meaning that they do not have a lot of bits set to 1.
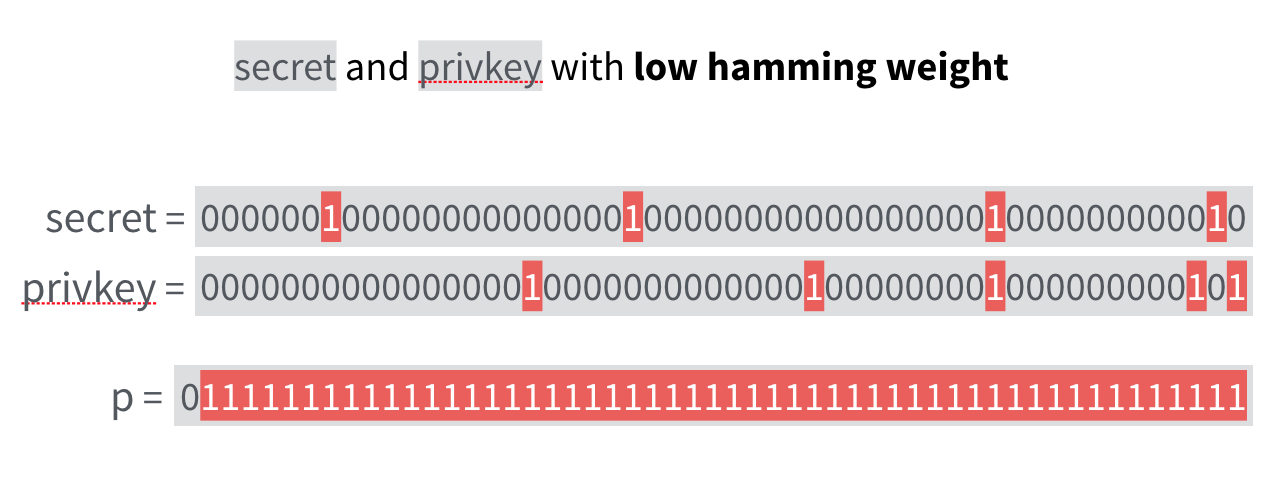
Now something very intuitive happens: the inverse of such a bitstring will probably have a high hamming weight, which let us believe that \(secret \cdot privkey^{-1} \pmod{p}\) looks random. This will be our public key.
Now that we have a private key and a public key. How do we encrypt ?
The paper starts with a very simple scheme on how to encrypt a bit \(b\).
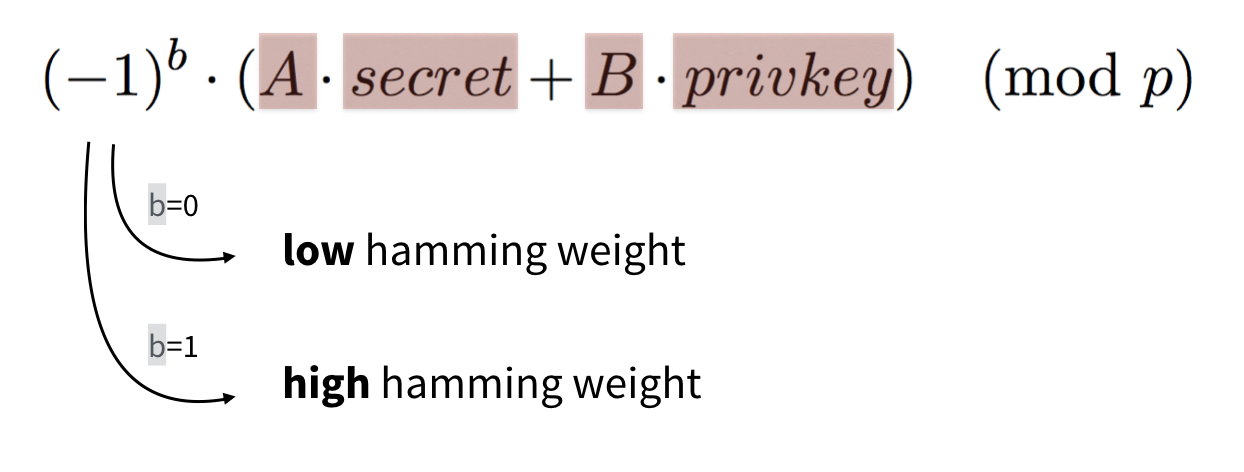
\[ciphertext = (-1)^b \cdot ( A \cdot pubkey + B ) \pmod{p} \]
with \(A\) and \(B\) two public numbers that have low hamming weights as well.
We can see intuitively that the ciphertext will have a high hamming weight (and thus might look random).
If you are not convinced, all of this is based on actual proofs that such operations between low and high hamming weight bitstrings will yield other low or high hamming weight bitstrings. All of this really work because we are modulo a \(1111\cdots\) kind of number. The following lemmas taken from the paper are proven in section 2.1.
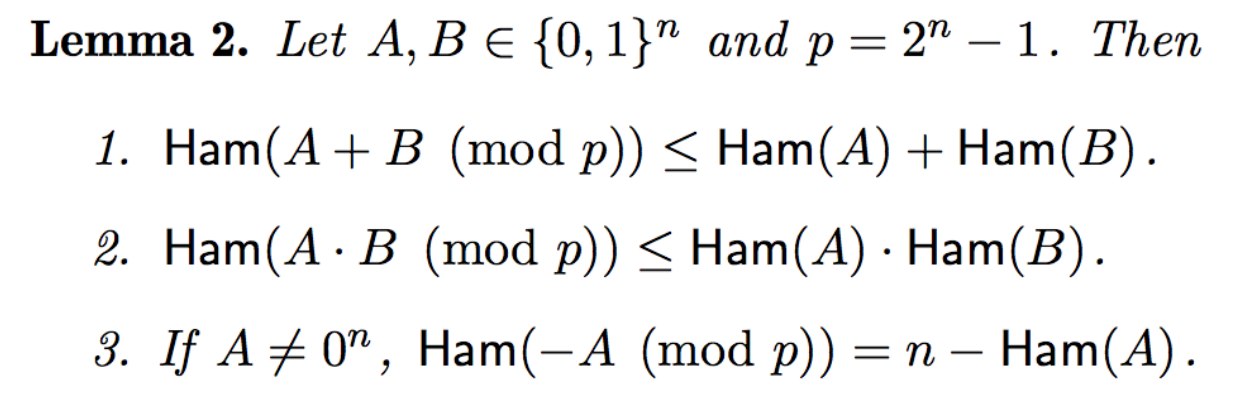
How do you decrypt such an encrypted bit?
This is how:
\[ciphertext \cdot privkey \pmod{p}\]
This will yield either a low hamming weight number → the original bit \(b\) was a \(0\),
or a high hamming weight number → the original bit \(b\) was a \(1\).
You can convince yourself by following the equation:

And again, intuitively you can see that everything is low hamming weight except for the value of \((-1)^b\).
This scheme doesn't look CCA secure nor practical. The paper goes on with an explanation of a more involved cryptosystem in section 6.
EDIT: there is already a reduction of the security estimates published on eprint.


Comments
leave a comment...