A pretty fresh article on how you could use crypto to replace a lot of complicated schemes you might use on your website like password reset or mail confirmation:
https://neosmart.net/blog/2015/using-hmac-signatures-to-avoid-database-writes/
tl;dr: instead of creating a table for tokens, you could create the password reset url like this:
http://www.example.com/password_reset/?user=username&expires=15649848949849&[email protected]&token=
and at the place of the token you would put the output of a MAC. Checking the MAC again after receiving the url would confirm that YOU created that url and it has not been modified. Remember, MAC provides integrity and authentication. The author also provides a way to only render this usable once: use the original hashed password as a nonce.
After some evidences of the Silk Road trial got out, Gwern noticed a PGP key was in here...
This is the ASCII-armored private key of the main DPR public key, the one he signed forum posts with and messaged with people. I was surprised to see it screenshotted like that, and I thought it would be hilarious if I could take the private key and announce that I was actually the real DPR by signing it with his key (since I've occasionally been accused of it).
more on the story here
I'm using cmder on windows, it's pretty and it comes with a lot of unix tools (cat, ls, bash, ssh, more, grep...) and pipes and streams and... I can use vim in the console. Not emacs, vim. I do have emacs on windows but I don't think I can do a emacs -nw to just use it from the console. So let's go back to learn vim, because I hate being slow. And here is a nice way of doing it!
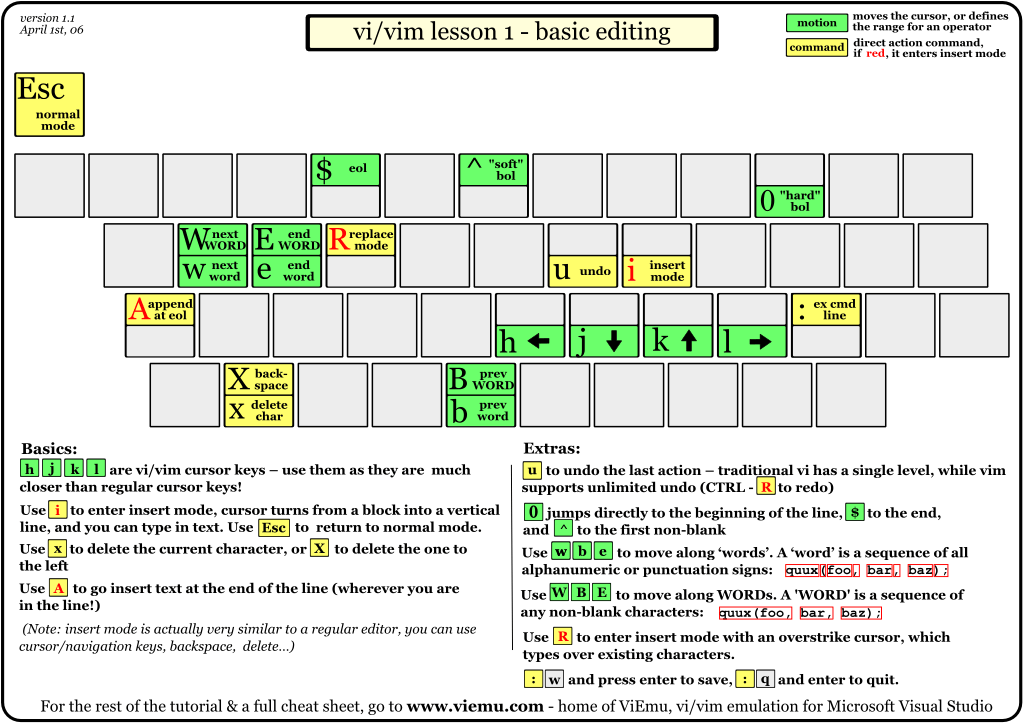
http://www.viemu.com/a_vi_vim_graphical_cheat_sheet_tutorial.html
you can find several pictures of a keyboard aiming at teaching you step by step how vim works. This is all I needed!
Silk Road's trial just closed and I ran into this old (?) journal of Ross Ulbricht that contains quite a bunch of interesting passages. I think this will turn into a movie.
03/25/2013
server was ddosed, meaning someone knew the real IP. I assumed they obtained it by becoming a guard node. So, I migrated to a new server and set up private guard nodes. There was significant downtime and someone has mentioned that they discovered the IP via a leak from lighttpd.
03/28/2013
being blackmailed with user info. talking with large distributor (hell's angels).
03/29/2013
commissioned hit on blackmailer with angels
04/01/2013
got word that blackmailer was excuted
created file upload script
started to fix problem with bond refunds over 3 months old
04/02/2013
got death threat from someone (DeathFromAbove)
04/04/2013
withdrawals all caught up
made a sign error when fixing the bond refund bug, so several vendors had very negative accounts.
switched to direct connect for bitcoin instead of over ssh portforward
received visual confirmation of blackmailers execution
04/06/2013
gave angels go ahead to find tony7
04/08/2013
sent payment to angels for hit on tony76 and his 3 associates
04/21 - 04/30/2013
market and forums under sever DoS attack. Gave 10k btc ransom but attack continued.
05/04/2013
attacker agreed to stop if I give him the first $100k of revenue and $50k per week thereafter. He stopped, but there
appears to be another DoS attack still persisting
05/07/2013
paid $100k to attacker
05/22/2013
paid the attacker $50k
05/29/2013
rewrote orders page
paid attacker $50k weekly ransom
$2M was stolen from my mtgox account by DEA
09/19 - 09/25/2013
red got in a jam and needed $500k to get out. ultimately he convinced me to give it to him, but I got his ID first and
had cimon send harry, his new soldier of fortune, to vancouver to get $800k in cash to cover it. red has been mainly
out of communication, but i haven't lost hope. Atlantis shut down. I was messaged by one of their team who said they
shut down because of an FBI doc leaked to them detailing vulnerabilities in Tor.
09/30/2013
Had revelation about the need to eat well, get good sleep, and meditate so I can stay positive and productive.
All of this sounds so surreal. He is making a huge amount of money for sure. A million dollars doesn't seem much for him. He is constantly buying servers and he seems to be coding a lot. He also seem like a normal dude.
And here's a funny thread on who's Variety Jones
here's an entertaining piece about NSA backdoors through history: http://ethanheilman.tumblr.com/post/70646748808/a-brief-history-of-nsa-backdoors
1997 Lotus Notes: The NSA requested that Lotus weaken its cryptography so that the NSA could break documents and emails secured by Lotus notes. This Software was used by citizens, companies and governments worldwide.
I talked about this one here.
from wikipedia:
A kleptographic attack is an attack which uses asymmetric encryption to implement a cryptographic backdoor. For example, one such attack could be to subtly modify how the public and private key pairs are generated by the cryptosystem so that the private key could be derived from the public key. In a well-designed attack, the outputs of the infected cryptosystem would be computationally indistinguishable from the outputs of the corresponding uninfected cryptosystem. If the infected cryptosystem is a black-box implementation such as a hardware security module, a smartcard, or a Trusted Platform Module, a successful attack could go completely unnoticed.
I've seen implementations of this in the wild, here on reddit (python) and here on lobsters (C#)
Here's a funny topic on CS Theory StackExchange: https://cstheory.stackexchange.com/questions/4491/powerful-algorithms-too-complex-to-implement?newreg=dbe44b3dd8ca41019f6a4a23b9fea6d3
What are some algorithms of legitimate utility that are simply too complex to implement?
Here's an awesome explanation of shellshock: https://bitbucket.org/carter-yagemann/shellshock/src/f0a88573f912?at=master
This repository contains useful documents which I have written to help educate the cybersecurity community on the "ShellShock" bash vulnerability. These documents are designed to help facilitate learning, including on how to identify possibly vulnerable services and how to remediate such vulnerabilities.
It's actually the clearest explanation I've seen on the subject.
Made by these guys from Syracuse:
- Carter Yagemann
- Amit Ahlawat


